 The digital world in 2025 is faster, smarter, and more connected than ever and so are the threats that lurk within it. Every connected device, from your smart coffee machine to global enterprise servers, is a potential target. The evolution of artificial intelligence, remote work systems, and global cloud adoption has opened a new battlefield where cybercriminals move quicker than traditional defenses.
The digital world in 2025 is faster, smarter, and more connected than ever and so are the threats that lurk within it. Every connected device, from your smart coffee machine to global enterprise servers, is a potential target. The evolution of artificial intelligence, remote work systems, and global cloud adoption has opened a new battlefield where cybercriminals move quicker than traditional defenses.
According to a 2025 Gartner report, cyberattacks now cost businesses an estimated $10.5 trillion annually worldwide nearly triple the figure from 2015. What’s changing isn’t just the volume of attacks, but their sophistication. Today’s hackers don’t just steal data; they hijack identities, manipulate voices, and weaponize artificial intelligence itself.
This article unpacks the latest cybersecurity threats shaping 2025 and explores how businesses are adapting using smarter tools, employee training, and proactive digital strategies to stay one step ahead.
Why Cybersecurity Threats Are Growing in 2025
The world is experiencing a perfect storm: more devices, more automation, and more dependence on digital systems. Every new innovation from IoT sensors in warehouses to cloud-based AI analytics adds both value and risk.
Three forces are driving the surge in cyber threats:
| Problem | Cause | Impact |
|---|---|---|
| Expanding attack surface | Billions of new IoT and AI-connected devices | More entry points for hackers |
| Human vulnerability | Remote work, phishing fatigue, poor cyber hygiene | Increased social engineering success |
| Advanced cyber tools | AI-based malware and automated hacking kits | Faster, more unpredictable attacks |
The reality is that cyber threats have outgrown old-fashioned defenses. Firewalls and antivirus software alone can’t keep up. Attackers now use machine learning to probe for weaknesses, while deepfake scams exploit human trust.
And as global conflicts shift into digital arenas, state-sponsored hacking is becoming a new form of cyber warfare. In short, the future of cybersecurity isn’t just about protection it’s about prediction.
The Biggest Cybersecurity Threats Right Now
Let’s look at the most dangerous and widespread threats defining 2025. Each one shows how cybercrime has evolved from blunt attacks to subtle, AI-powered deception.
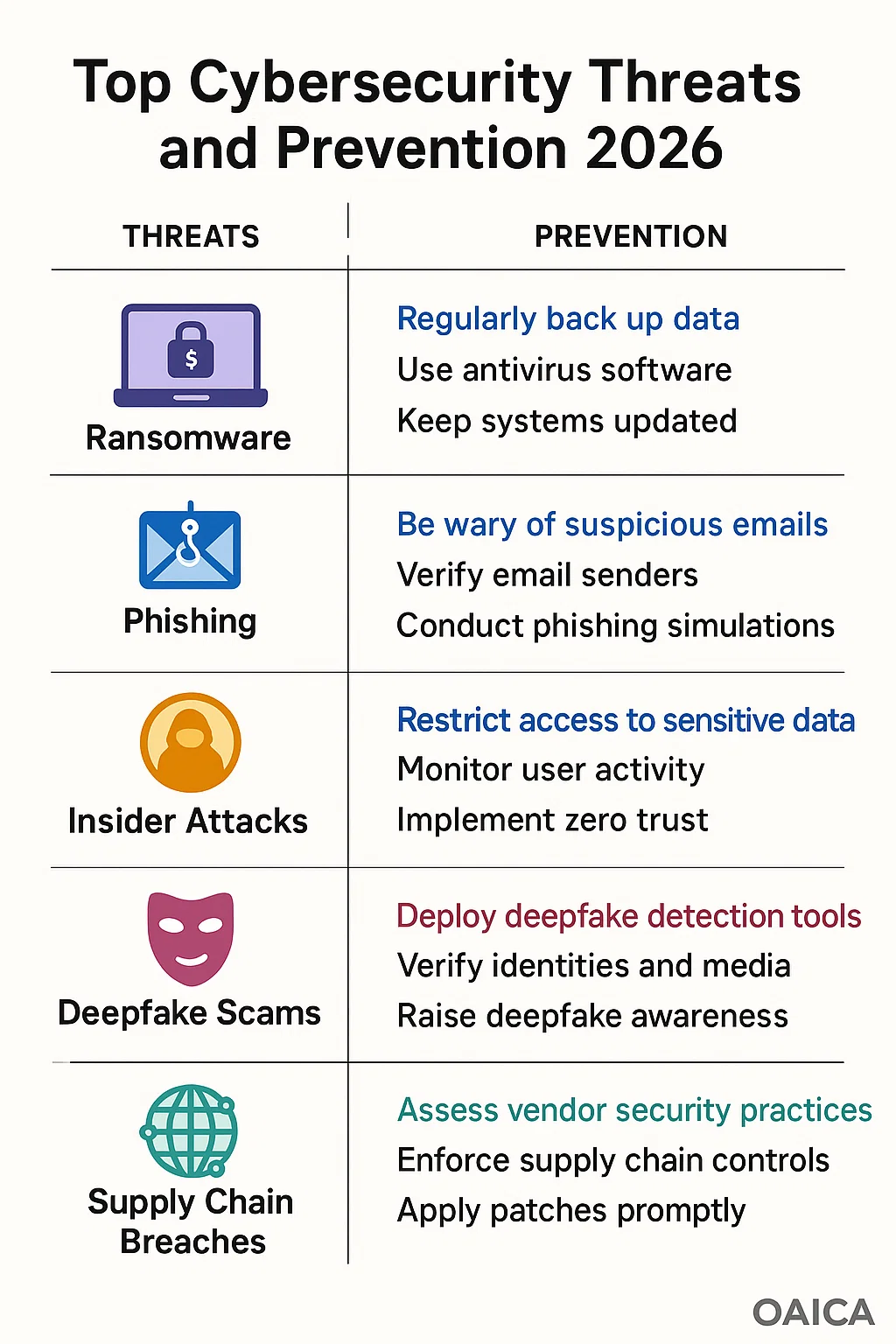
Ransomware Reinvented with AI
Ransomware is no longer just a digital lock on your data it’s now a precision-guided weapon. Cybercriminals use AI algorithms to customize attacks, selecting targets based on how likely they are to pay.
In early 2025, a major logistics company in Europe suffered an AI-driven ransomware breach. The malware first analyzed the company’s financial reports, then demanded a “realistic” ransom amount within their annual budget range making it seem disturbingly rational.
Businesses are countering this trend by implementing Zero Trust frameworks and automated backup verification ensuring they can restore operations without negotiating with criminals.
Phishing 3.0 Deepfake and Voice Cloning Scams
Forget the old email scams. Today’s phishing involves AI-generated voices, cloned executives, and fake video calls. Criminals now mimic CEOs or CFOs to authorize money transfers or release confidential data.
For example, a multinational bank recently lost $25 million when an AI-cloned voice convinced an employee that their CFO was on the line. The realism was chilling.
To fight back, businesses are adopting multi-layered verification and voice authentication protocols, alongside employee training programs to recognize even subtle signs of deception.
Supply Chain Attacks Targeting Vendors
Cybercriminals have realized that breaking into a large company is hard but breaching a smaller partner is easier. These supply chain attacks target third-party software or vendors, injecting malicious code into trusted updates.
The 2024 “SolarGate 2.0” incident, for example, compromised over 50 organizations via a single software vendor. The ripple effects were global.
In 2025, companies are securing their digital supply chains by auditing vendor access, using AI-driven code scanning, and demanding cyber compliance certificates from all partners.
Insider Threats and Human Errors
Despite all the technology, humans remain the weakest link. Employees accidentally clicking malicious links or reusing passwords still account for nearly 60% of corporate breaches, according to IBM’s 2025 Cybersecurity Report.
Some insider threats are unintentional; others are deliberate such as disgruntled workers selling credentials on the dark web.
Businesses now use behavioral analytics to detect unusual activity, and privilege segmentation to limit access to sensitive systems.
State-Sponsored Cyber Espionage
From power grids to hospital databases, state-backed hackers are targeting critical infrastructure. These campaigns are often politically motivated and use custom-built malware that bypasses traditional detection systems.
In 2025, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) reported a rise in AI-generated malware designed to learn and adapt mid-attack effectively outsmarting traditional antivirus tools.
To defend against these, organizations are forming public-private cybersecurity alliances and sharing threat intelligence across sectors faster than ever before.
Who Is Behind the Recent Cyber Attacks?
Cyberattacks today come from a complex mix of sources and not all of them are shadowy figures in dark rooms.
- Organized Crime Syndicates
- Run ransomware-as-a-service (RaaS) operations.
- Employ programmers, negotiators, and even PR managers.
- Hacktivist Groups
- Target corporations for political or social causes.
- Use defacement or data leaks as protest tools.
- Nation-State Actors
- Engage in long-term cyber espionage campaigns.
- Aim to disrupt rivals’ economies or steal defense data.
- Solo Hackers and AI Enthusiasts
- Experiment with open-source AI hacking tools for fame or curiosity.
- Sometimes accidentally trigger massive disruptions.
Recent high-profile examples include the 2025 “BlackHarbor” attack, which targeted energy infrastructure across North America, and the “PhantomEye” breach, exposing data from over 40 million e-commerce customers worldwide.
How Businesses Are Responding to Modern Threats
Forward-thinking businesses are no longer waiting to be attacked they’re building resilience from the inside out.
AI-Driven Threat Detection and Zero Trust Architecture
Instead of relying on human analysts alone, companies are using AI-powered detection systems to scan millions of data points per second. Platforms like Microsoft Sentinel and CrowdStrike Falcon now integrate predictive analytics that can identify abnormal behavior before an attack hits.
The Zero Trust model “never trust, always verify” has become the global standard. Every device, user, and request must authenticate continuously. This approach drastically limits lateral movement after a breach.
Investing in Employee Cyber Awareness
Technology can’t fix what training can prevent. Businesses are rediscovering the human side of cybersecurity.
Modern awareness programs include interactive simulations, gamified phishing tests, and even AI-powered learning bots that coach employees through real-life scenarios.
One small accounting firm in Canada reported a 70% reduction in phishing click rates after six months of gamified training proving that education is still the best firewall.
Strengthening Endpoint Security and Cloud Protection
With hybrid work here to stay, the “office” is now everywhere. That’s why endpoint security securing every laptop, phone, and server is crucial.
Tools like SentinelOne, ESET Protect, and Google Chronicle combine endpoint protection with cloud analytics. They monitor for malware, data leaks, and compliance issues across multiple devices.
Cloud providers have also stepped up. Amazon Web Services and Microsoft Azure now offer AI-led threat modeling that automatically isolates compromised instances before damage spreads.
Partnering with Managed Security Service Providers (MSSPs)
Not every business can afford an in-house security team. That’s where MSSPs come in external experts who provide 24/7 monitoring, threat hunting, and response services.
For small businesses, MSSPs offer enterprise-grade protection at a fraction of the cost. Many now include real-time dashboards, allowing owners to track their security posture visually.
Case Studies Real-World Lessons from Cyber Incidents
Case 1: Ransomware in Healthcare
A regional hospital network in Asia faced a ransomware attack that locked patient files. Because they had verified cloud backups and segmented networks, recovery took just 24 hours no ransom paid.
Lesson: Backups are your best insurance. Test them regularly.
Case 2: Supply Chain Breach in E-Commerce
A small online retailer was hit after a vendor’s plugin update included malicious code. The attack stole customer payment data for weeks unnoticed.
Response: They switched to AI code validation tools and vendor screening. Now, every update passes through automated integrity checks.
So, Trust must be verified continuously even with long-term partners.
Case 3: Phishing Leak in Finance
A financial firm lost client data due to a fake CEO email. They introduced multi-step approval workflows and voice biometrics for transactions.
Lesson: Secure systems fail if people don’t double-check what looks familiar.
Advanced Tools and Technologies to Watch
2025 is witnessing a major leap in cybersecurity innovation. Here are a few technologies changing how businesses defend themselves:
- AI Cyber Defense Platforms: Use self-learning algorithms to detect new threats automatically.
- Quantum Encryption: Emerging as a game-changer for unbreakable data transmission.
- Passwordless Authentication: Biometrics and security keys replacing traditional passwords.
- Predictive Analytics: Anticipating threats before they occur using data trends.
- Decentralized Identity Systems: Using blockchain to verify users without storing central credentials.
Companies investing in these technologies are seeing reduced breach recovery times and improved regulatory compliance a strong competitive advantage in digital trust.
Expert Insights and Industry Predictions
Cybersecurity experts agree: AI is both the problem and the solution.
“We’re entering an era where AI can generate an entire cyberattack autonomously but it can also stop one before a human notices,”
Dr. Elaine Hughes, Gartner Senior Analyst (2025)
Cisco’s 2025 Threat Report predicts that over 60% of global enterprises will use AI-driven defense systems by 2026. Meanwhile, Symantec warns that deepfake-based fraud could become the single largest source of corporate identity theft within two years.
The future isn’t about eliminating risk it’s about responding faster, smarter, and together.
Practical Cyber Hygiene Checklist for Businesses
Here’s a quick, printable checklist to strengthen your company’s cyber resilience:
| Task | Frequency | Purpose |
|---|---|---|
| Update all software and firmware | Weekly | Patch known vulnerabilities |
| Backup critical data (encrypted) | Daily | Prevent ransomware lockouts |
| Conduct phishing simulations | Monthly | Train staff to detect scams |
| Review vendor access permissions | Quarterly | Reduce third-party risks |
| Implement MFA (multi-factor authentication) | Always | Stop unauthorized logins |
| Audit network logs and endpoints | Weekly | Spot unusual activities early |
| Use a password manager | Always | Avoid weak or reused passwords |
Final Thoughts Before You Secure Your Business
Cybersecurity in 2025 is no longer an IT issue it’s a leadership issue. The most successful organizations treat security as culture, not compliance. They empower teams, integrate AI tools, and plan for resilience instead of panic.
The threats are evolving fast, but so are the defenses. Whether you’re a small café owner or a global enterprise, your best strategy is constant learning and adaptation.
As the old saying in cybersecurity goes: It’s not about if you’ll be attacked it’s about how prepared you’ll be when it happens.
